How Approov Mobile Security protects your mobile apps and APIs
Approov Mobile Security is a run-time application self protection (RASP) technology, enabling software attestation, and designed specifically for use within mobile applications running on iOS and Android. Approov creates a trusted environment to ensure that the mobile app connecting through an API is a genuine, untampered instance, fraudulent transactions, malicious scripts, and bot attacks are blocked at the source.
The Approov service employs a challenge-response cryptographic protocol to verify the authenticity of a connecting client application. This approach differs fundamentally from other solutions because it does not rely on any secret embedded within the app. Instead, it dynamically assesses the integrity of the app to determine its nature rather than what it possesses as a static secret. Approov is designed to authenticate individual app instances, not users.
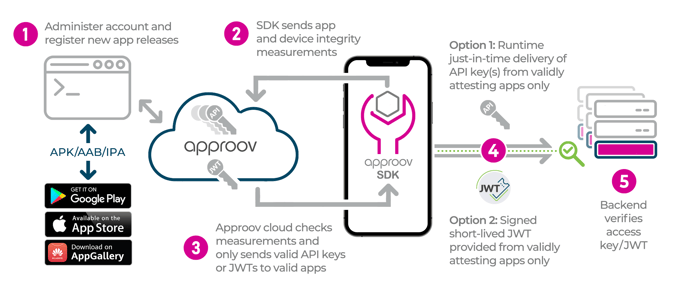
The mobile app registration process involves using the Approov CLI tool to analyze and create a unique signature for the app, adding it to the Approov cloud service. This unique signature, or "DNA," is used to recognize the app as official without storing its code. Before each API request made by the app, the Approov SDK is called, and if no cached token is available, an integrity assessment process is initiated. This process involves the SDK and Approov cloud service working together to verify that the app and its runtime environment are legitimate and free from malicious activity. The SDK gathers the material used for the assessment and the cloud service makes a decision based on your security policy criteria, issuing a valid cryptographically signed Approov token if criteria are met. The token is cached by the SDK for up to 5 minutes and automatically refreshed before expiry or when the app’s runtime environment changes. Communication is securely pinned to prevent interception.
On the API backend, the validity of Approov tokens is checked to ensure requests are from an official, unmodified app and not from scripts, bots, or compromised environments. Since the signing key is not in the app, attackers cannot reverse engineer it to create their own signed tokens. Requests failing the token check are likely from unauthorized sources, and you can configure your backend to block them.
